Just noticed that Reliance Jio (AS55836) seems to be originating a /16 which is for Charter Communications (AS20115) - 47.35.0.0/16.
route-views>sh ip bgp 47.35.0.0/16 long | exclude 20115
BGP table version is 18764390, local router ID is 128.223.51.103
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
* 47.35.0.0/16 195.208.112.161 0 3277 3267 174 64049 55836 i
* 217.192.89.50 0 3303 6762 64049 55836 i
* 212.66.96.126 0 20912 1267 64049 55836 i
* 162.243.188.2 0 393406 6453 6762 64049 55836 i
* 192.241.164.4 0 62567 2914 174 64049 55836 i
* 129.250.0.11 1007 0 2914 174 64049 55836 i
* 104.192.216.1 0 46450 174 64049 55836 i
* 202.93.8.242 0 24441 3491 3491 174 64049 55836 i
* 66.59.190.221 0 6539 577 6762 64049 55836 i
* 144.228.241.130 80 0 1239 174 64049 55836 i
* 207.172.6.20 0 0 6079 3356 174 64049 55836 i
* 203.62.252.83 0 1221 4637 174 64049 55836 i
* 93.104.209.174 0 58901 51167 3356 6762 64049 55836 i
Network Next Hop Metric LocPrf Weight Path
* 162.250.137.254 0 4901 174 64049 55836 i
* 4.69.184.193 0 0 3356 174 64049 55836 i
* 208.51.134.254 1 0 3549 3356 174 64049 55836 i
* 89.149.178.10 10 0 3257 174 64049 55836 i
* 66.110.0.86 0 6453 6762 64049 55836 i
* 134.222.87.1 650 0 286 174 64049 55836 i
* 95.85.0.2 0 200130 6453 174 64049 55836 i
* 12.0.1.63 0 7018 174 64049 55836 i
* 173.205.57.234 0 53364 3257 174 64049 55836 i
* 206.24.210.80 0 3561 174 64049 55836 i
* 5.101.110.2 0 202018 2914 174 64049 55836 i
* 207.172.6.1 0 0 6079 3356 174 64049 55836 i
* 154.11.98.225 0 0 852 174 64049 55836 i
* 194.85.40.15 0 3267 174 64049 55836 i
* 208.74.64.40 0 19214 174 64049 55836 i
* 209.124.176.223 0 101 101 174 64049 55836 i
* 66.185.128.48 6 0 1668 174 64049 55836 i
* 203.181.248.168 0 7660 2516 6762 64049 55836 i
* 202.232.0.2 0 2497 701 6762 64049 55836 i
* 103.247.3.45 0 58511 64049 55836 i
* 193.0.0.56 0 3333 1103 64049 55836 i
Network Next Hop Metric LocPrf Weight Path
* 80.241.176.31 0 20771 47872 64049 55836 i
*> 216.218.252.164 0 6939 64049 55836 i
* 132.198.255.253 0 1351 174 64049 55836 i
* 103.255.249.22 0 58443 45177 64049 55836 i
* 114.31.199.1 0 4826 174 64049 55836 i
route-views>
This shows Reliance Jio’s ASN AS55836 announcing 47.35.0.0/16. Charter Communications (AS20115) is originating multiple of /18s out of the same pool.
 Today Google (
Today Google (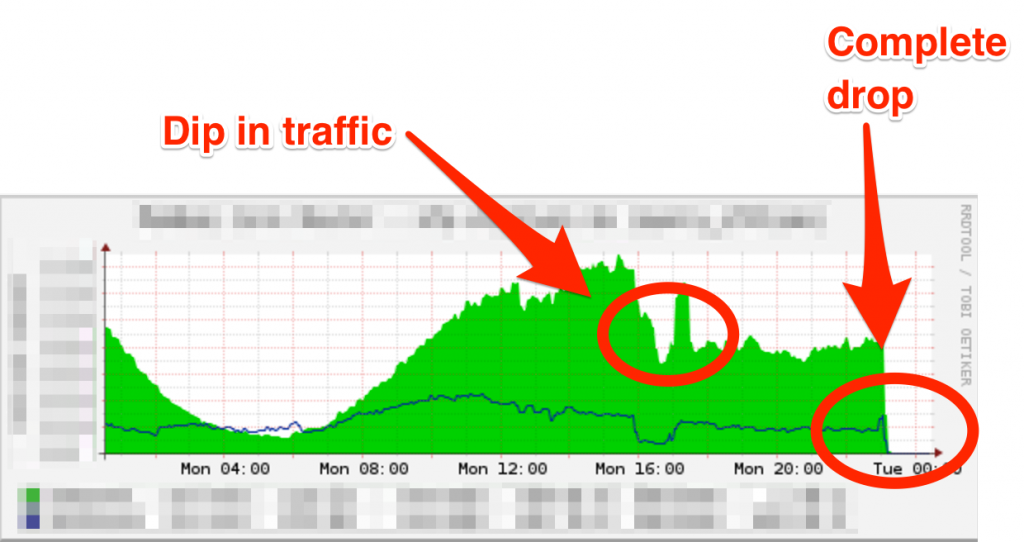 This shows how traffic of an ISP connected to Google in Mumbai dipped during peak time around at 4pm on Monday 12th Dec (IST) and went to zero little before midnight. I triggered a trace to aspmx.l.google.com. which is outside India from
This shows how traffic of an ISP connected to Google in Mumbai dipped during peak time around at 4pm on Monday 12th Dec (IST) and went to zero little before midnight. I triggered a trace to aspmx.l.google.com. which is outside India from  One of frequent email and
One of frequent email and  Bangladesh’s .bd ccTLD faced another outage. As I mentioned in one of the
Bangladesh’s .bd ccTLD faced another outage. As I mentioned in one of the  Day before yesterday i.e on 18th August 2016 Bangladesh’s TLD .bd went had an outage. It was originally reported by Jasim Alam on
Day before yesterday i.e on 18th August 2016 Bangladesh’s TLD .bd went had an outage. It was originally reported by Jasim Alam on