Letsencrypt - Free signed automated SSL
Last year a really good project Letsencrypt came up. They key objective of this project is to help in securing web by pushing SSL everywhere.
Two key cool features
- It offer free signed SSL certs!
- It helps in setting up SSL via an agent seamlessly without having to deal with CSR, getting it signed & updating web server configuration.
At this stage Letsencrypt is itself a Certificate Authority and but it’s root certs are yet not in the browser. It’s probably going to take a while till all major browsers get their certificate. To help on that one of it’s sponsors IdenTrust has signed their intermediate certs. Hence certs signed by Letsencrypt are accepted by all browsers right away. All certs signed by Letsencypt are signed by Letencrypt Authority X1 which have signature from DST Root CA X3 which is accepted by pretty much all popular browsers. You can read more about How it works here. Here’s an example of SSL setup for say “demo.anuragbhatia.com” test domain which is already up and working without SSL. http://demo.anuragbhatia.com shows a plain text page. This is Apache running on Ubuntu server. The Apache web config is pretty straightforward.
<VirtualHost \*:80>
ServerName demo.anuragbhatia.com
DocumentRoot /var/www/demo.anuragbhatia.com
ErrorLog /var/log/apache2/demo.anuragbhatia.com
LogLevel notice
</VirtualHost>
Step 1 - Grab the Letscrypt agent git clone https://github.com/letsencrypt/letsencrypt Step 2 - Execute the auto script ./letsencrypt-auto –help This will grab all needed dependencies and will get the agent working. Step 3 - Execute Letsencrypt auto script with it’s Apache plugin ./letsencrypt-auto –apache -d demo.anuragbhatia.com It takes with a quick wizard and in the end I get:
Congratulations! You have successfully enabled https://demo.anuragbhatia.com
You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=demo.anuragbhatia.com
And it’s done! Wizard got me a signed SSL and installed it in the apache config as well.
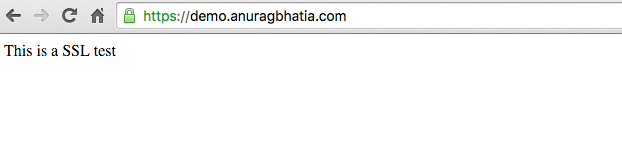
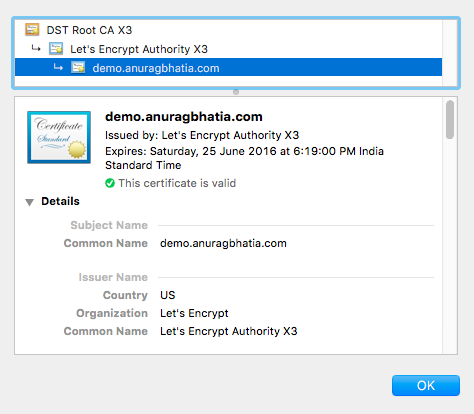
The agent created an addional Apache config with name demo.anuragbhatia.com-le-ssl.conf with following content
<IfModule mod\_ssl.c>
<VirtualHost \*:443>
ServerName demo.anuragbhatia.com
DocumentRoot /var/www/demo.anuragbhatia.com
ErrorLog /var/log/apache2/demo.anuragbhatia.com
LogLevel notice
SSLCertificateFile /etc/letsencrypt/live/demo.anuragbhatia.com/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/demo.anuragbhatia.com/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
SSLCertificateChainFile /etc/letsencrypt/live/demo.anuragbhatia.com/chain.pem
</VirtualHost>
</IfModule>
Here options-ssl-apache.conf plays an important role by using better security options. It’s config:
# Baseline setting to Include for SSL sites
SSLEngine on
# Intermediate configuration, tweak to your needs
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA
SSLHonorCipherOrder on
SSLCompression off
SSLOptions +StrictRequire
# Add vhost name to log entries:
LogFormat "%h %l %u %t \\"%r\\" %>s %b \\"%{Referer}i\\" \\"%{User-agent}i\\"" vhost\_combined
LogFormat "%v %h %l %u %t \\"%r\\" %>s %b" vhost\_common
CustomLog /var/log/apache2/access.log vhost\_combined
LogLevel warn
ErrorLog /var/log/apache2/error.log
# Always ensure Cookies have "Secure" set (JAH 2012/1)
#Header edit Set-Cookie (?i)^(.\*)(;\\s\*secure)??((\\s\*;)?(.\*)) "$1; Secure$3$4"
Some of the limitations
- Signed SSL certs are valid only for 90 days and have to be renewed.
- Wildcard SSL certs are not supported yet.
- IPv6 is not supported in the autoconfig setup via client. One can always get certificate manually and use with IPv6 but agent is yet to support IPv6 (which I guess is from next month).
You can read more on their excellent documentation here and can also consider checking Presentation by Ashley Jones from PCH at SANOG on All TLS, all the time. Have fun!